As security experts wage an unending battle against cyber thieves, massive data breaches (like those that rocked Target, Anthem and Best Buy) are still a threat as newer and more clever forms of malware attempt to invade the very systems designed to keep our data safe.
Since point of sale (POS) terminals process millions of credit and debit card purchases every day, the lucrative nature of these targets has motivated criminals to infiltrate POS systems with ever evolving forms of malware.
Through viruses like AbaddonPOS – a malware strain that showed up late last year and then emerged again in May, with fancy new tricks to lure users into installing it – criminals can capture cardholder names, credit card numbers, expiration dates and even verification codes. Such forms of card-scraping malware have recently afflicted the Hard Rock Hotel & Casino, the Trump Hotel Collection, Hilton and Starwood Hotels and even restaurant chains like Wendy’s.
And since POS hacks thrive on consumer data, the approaching holiday shopping season is a particularly enticing time for cybercriminals to flood businesses with newer, more powerful POS malware that can capture consumer credit and debit card transactions. In recent years, security experts have discovered more than a dozen new families of POS malware, including NitlovePos, PoSeidon, MWZLesson, MalumPOS, and AbaddonPOS.
What is AbaddonPOS?
First discovered in the fall of 2015 by Proofpoint cyber security researchers, AbaddonPOS was spotted when a POS terminal infected with the Vawtrak banking Trojan was trying to download the harmful malware. Because Vawtrak and AbaddonPOS contain similar code, Proofpoint concluded the same hackers likely created them.
The Vawtrak virus spotted on the infected computer was attempting to download TinyLoader, a customized protocol that downloads payloads from a command and control server. Once TinyLoader copies itself, it downloads TinyDownloader in the form of shellcode, which is then used to download AbaddonPOS — a card-scraping malware designed to scan memory processes for payment information. The malware can infect POS terminals via the Angler exploit kit or through weaponized Microsoft Office documents.
Though small in size at 5KB, AbaddonPOS is quite sophisticated when compared to other forms of POS malware. The malware has been doctored to include basic anti-analysis and obfuscation properties, which makes it difficult to track using manual or automated analysis techniques. Once installed, AbaddonPOS searches for credit cards by reading the target system’s memory and sends the stolen data back to its command and control server using a custom binary code protocol instead of HTTP.
What was Old is now New Again
Like so many other viruses that make their big debut then go quiet, AbaddonPOS reinvented itself and came out with some new tricks in May of this year. According to security firm Proofpoint:
“On May 5, a financially motivated actor whom Proofpoint has been tracking as TA530 (also featured in our previous blog post “Phish Scales” [1]) sent out a highly-personalized email campaign targeting primarily retail companies and attempting to install TinyLoader and AbaddonPOS point-of-sale malware. The retail vertical was likely chosen due to the higher likelihood of infecting a POS system. We first observed AbaddonPOS when it was delivered by Vawtrak [2] in October of 2015. We have also found that TinyLoader and AbaddonPOS have since been updated in several ways.”
While POS malware presents a real threat for any business owner, these viruses are particularly threatening for companies that use the same computers to check emails and process POS transactions. Proofpoint provided examples of how AbaddonPOS uses a work email to lure the recipient in to enabling content, which in turn downloads AbaddonPOS.
“The messages we observed used subjects such as ‘Group Booking at [company name]’ and the personalized
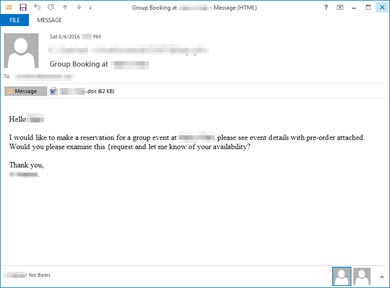
An example of a phishing email – AbaddonPOS
attachment names such as:
- [company name].doc
- [company name]_booking.doc
- [company name]_reservation.doc
The example message shown in Figure 1 uses the recipient’s name in the email body and the company’s name in the email body and the attachment name. The attachment, shown in Figure 2, uses an interesting lure. It depicts an image of a spinner one would expect to see when content is loading and asks the user to enable content.
Clicking the “Enable Content” button enables the malicious macro, which then begins the infection by downloading TinyLoader, which in turn downloads AbaddonPOS.
Most of the messages we saw were delivered to retail companies (Figure 3).”
Employee Training, Segmentation, and P2PE for Protection against Malware
While protecting POS environments can present financial and tactical challenges for many businesses, particularly those who need to fund large, security-based hardware updates, the most likely source of infection remains human error. Employees with a lack of security training can open an email with an attachment and unknowingly trigger an infection. Due to the relative sophistication of AbaddonPOS and its propensity to self-replicate, the malware could be installed on many devices without a merchant even noticing.
Since POS systems run on operating systems like Microsoft Windows and Linux, they are vulnerable to the same breaches as other desktops and servers. To protect POS systems from regular user networks, Internet connectivity to POS networks should be disconnected or severely limited through the use of point-to-point VPNs.
While many retailers and companies are switching to EMV chip cards – the microchips in EMV cards protect consumers and merchants from card cloning (“white-labeling”) and use at the POS – EMV has nothing to do with protecting the actual data once it leaves the card and enters the POS system. In order to keep data protected from the moment of transaction onward, businesses must employ point-to-point encryption (P2PE), which protects cardholder information by encrypting the data at the Point of Interaction (POI).
Bluefin provides PCI-validated P2PE solutions for mobile, point of sale, unattended and call center environments. PCI-validated P2PE solutions instantaneously convert confidential credit card data into indecipherable code as soon as the card is swiped, per the PCI SSC requirements for a validated solution, meaning that hackers cannot read or access any credit card data, even if they successfully breach the system.
Benefits of a PCI-validated P2PE solution for merchants include reduced PCI compliance scope, saving time and money on annual audits, avoidance of network segmentation, and the assurance that the technology has been vetted and approved by the PCI Security Standards Council (SSC). And as we discussed last week in the first part of our multi-series blog on the components of PCI-validated P2PE solutions, there are significant differences between non-validated and validated solutions, including Device Security, Encryption and Decryption protocols, Device Chain of Custody, and Device Management.
Bluefin’s Chief Innovation Officer, Ruston Miles, will speak at the PCI’s North America Annual Community Meeting next Tuesday on “How to Communicate PCI to the Boardroom,” including a discussion on prevention of security threats, such as malware with P2PE.








